Our website is not supported on this browser
The browser you are using (Internet Explorer) cannot display our content.
Please come back on a more recent browser to have the best experience possible

Although IT projects generally affect a portion of an organization using a new service or tools, security projects affect everyone, including partners. The shift in the C-Suite to include a Chief Information Security Officer (CISO) has become a meaningful change, and the emergence and even commonplace of DevSecOps are leading a further change.
As a result, Security Compliance PMOs are becoming a reality and will be a fundamental part of achieving successful outcomes.
PMOs have been around since the 90s. In general, they do not focus on security projects in most companies. While companies may have security talent and resources, it is pretty rare that they also have all the management skills necessary. Thus the security program is left void of the necessary PMO structure.
Organizations face increasing cyber risk today by working from home, using potentially unsecured devices, or using out-of-date virus protection. The onset of public cloud capabilities has led to vendors creating new channels and ways of protecting data, followed swiftly by businesses sponsoring many new projects. There are also many security options between new tools and services adoption in an ever-changing landscape of expanding technology platforms.
These new security solutions and policies can and will make a massive impact on businesses, yet these are often solutions that very few people understand and can explain. Quite often, highly technical practitioners fail to explain the business benefits of a security change, tool, or regulation.
Like any other business transformation, security transformation requires a disciplined project management approach to realize the expected benefits across an organization. Today’s business needs to visualize the value delivered by these security projects and or programs.
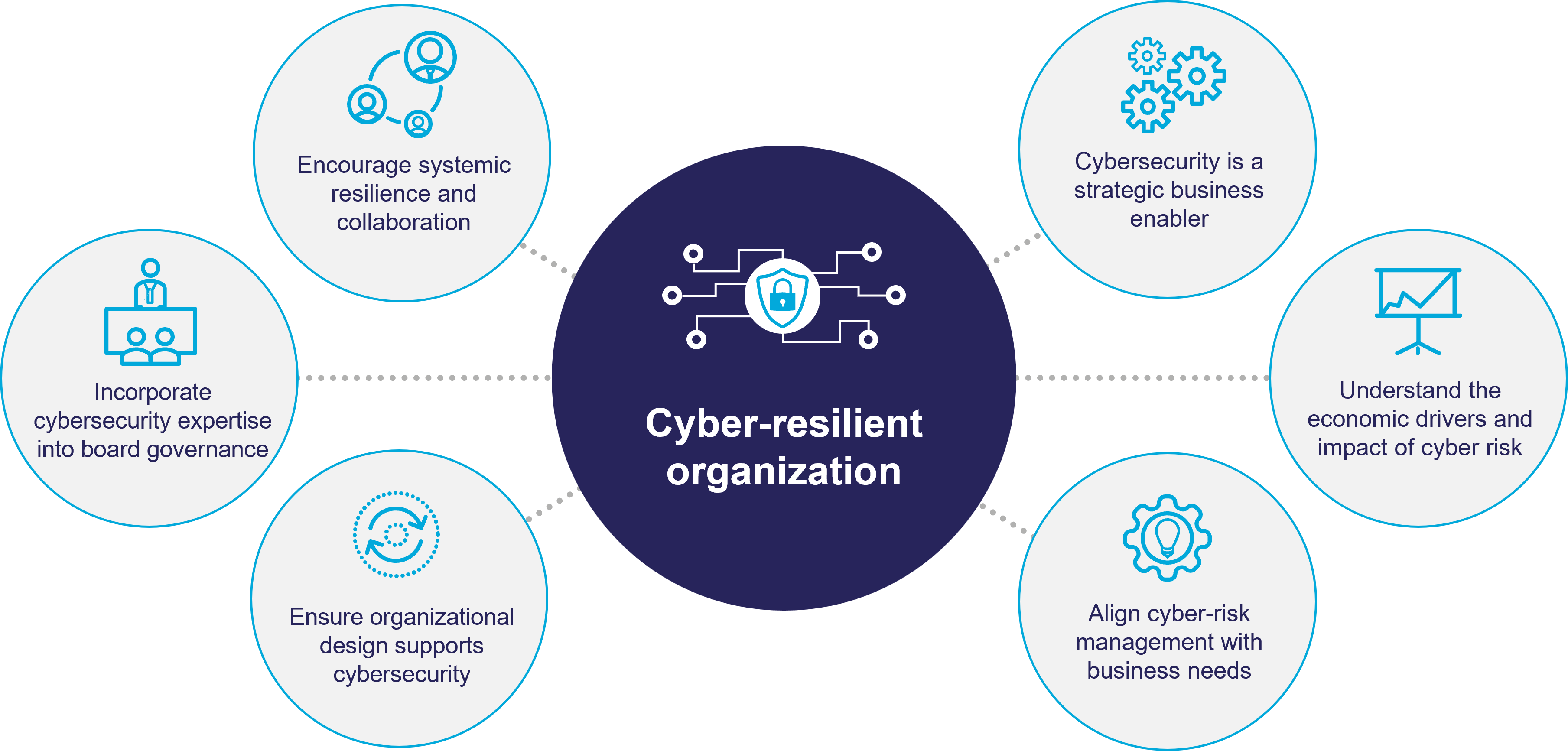
Security and compliance are linked because assets, infrastructure, and data are not located in a single on-premise data center. The organization model relies on different technical teams to work together. It is relevant in the business setting because collaboration between technical teams allows for the following:
With the ongoing remote and hybrid work, a unified approach is essential to manage vulnerabilities such as cloud usage, network infrastructure, personal device use, real risks with unvetted apps/platforms, and new vulnerabilities in existing apps or platforms.
For additional reading, visit Safeguard Cyber.
These risks are present and very real, and the threats at hand endanger an organization’s security and compliance. An adequate security and compliance PMO can empower enterprises to implement the following principles:
One of the challenges to manage is the high matrix nature of technology organizations; allocating resources to corporate cross-organizational projects is difficult. Therefore, establishing the Security and Compliance PMO is necessary, and organizations also require executive-level sponsorship to be efficient and effective. Here, the Security and Compliance PMO can provide the conduit between the IT PMO organization and the business.
We are seeing an increase in the need for security-focused Project Managers looking for a dedicated PMO function to support the ever-challenging IT environment to deliver Cyber Security projects successfully.
The definition of a PMO does not change – a PMO is an organizational structure used to standardize the portfolio, program, or project-related governance processes and facilitate sharing of resources, methodologies, tools, and techniques.
A Security & Compliance PMO has many key benefits, such as:
It will also need to work with an understanding of Cyber Security Frameworks (CSF) such as NIST, ISO27001, and ITIL.
For additional reading, visit US CyberSecurity Net and the US Cybersecurity Magazine.
A Cybersecurity PMO comprises six major components: Risk Management, Compliance, Policy and Procedure Management, Vulnerability Management, Security Project Management, and Knowledge Management.
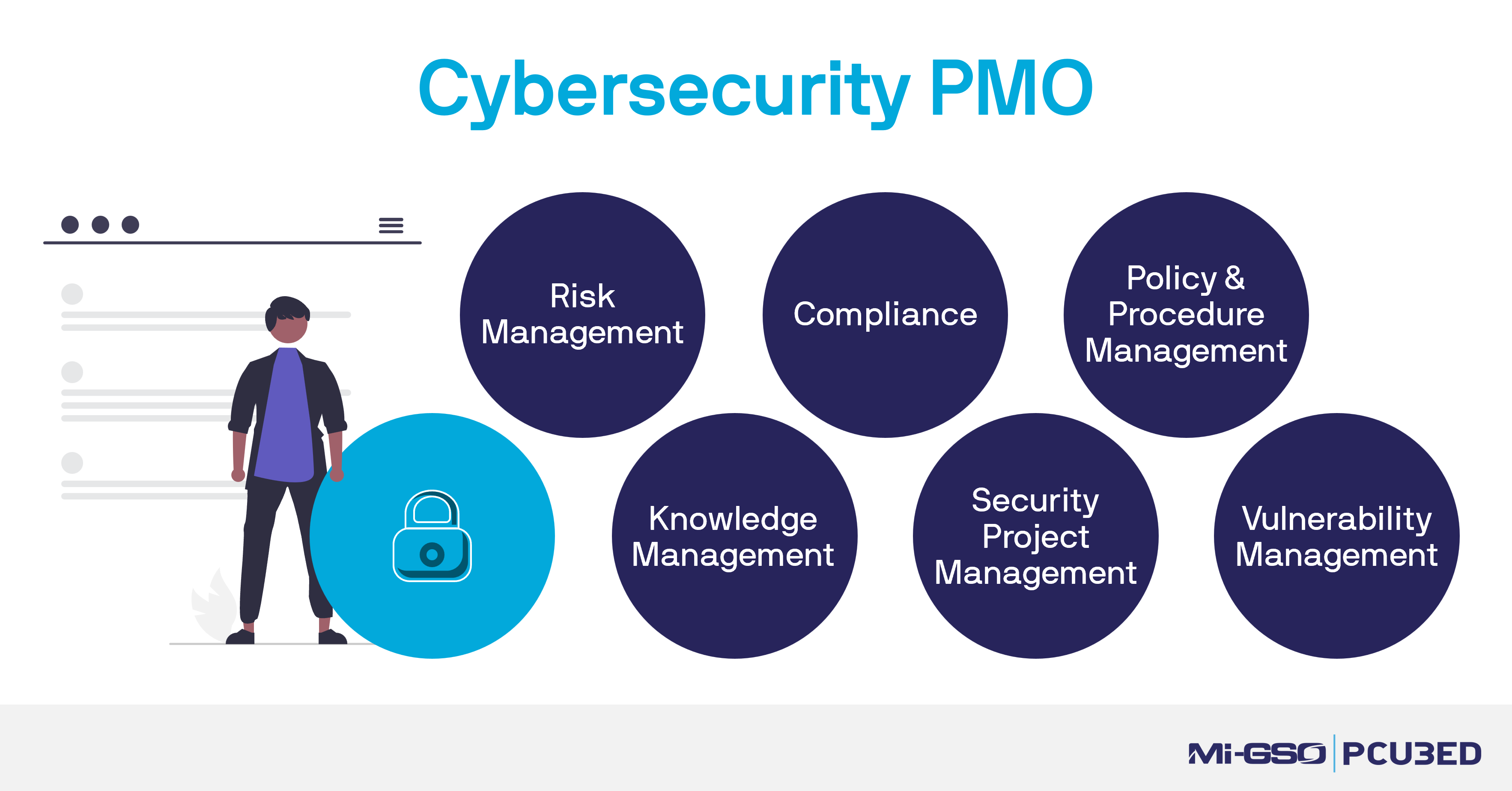
In addition to these components, setting up a Security and Compliance PMO must follow a well-established approach. To get started, take stock of assets essential to the business and understand the risk to those assets. If the security team is overwhelmed with day-to-day issues, and the only board reporting is on how the month’s problems will be resolved, set up a cybersecurity PMO to help restructure and manage the program.
Most importantly, the cybersecurity PMO can address the core pillars of Responsibility, Accountability, Transparency, Integrity, Awareness, Availability, Confidentiality, Performance, and Authenticity.
Contact us for more information about how to set up your Security & Compliance PMO, where we will provide more details on our suggested approach:
The CSF (Cyber Security Framework) focuses on cybersecurity decision-making as a function of business risk and defines the primary functions of a cybersecurity program as Identify, Protect, Detect, Respond and Recover.
Once business assets and risks are understood, measures can be implemented to mitigate business risks inherent to the operational environment. Protective measures include activities such as:
An example of projects that would be managed through the Security and Compliance PMO are as follows:
The Security and Compliance Operating Model will connect to the IT Operating Model to support Business growth.
Regardless of size, every organization needs a cybersecurity program focused on business success. Structuring around the NIST CSF and using the cybersecurity PMO organizational construct, every business can move cybersecurity from an unknown business risk to a business asset.
Don’t wait until after a significant breach to begin thinking about the structure of your program. For large businesses, doing nothing could be very costly, resulting in lost profits, productivity, and reputation.
This article was written by Alf Raju, Commercial Director at MIGSO-PCUBED USA.
Loved what you just read?
Let's stay in touch.
No spam, only great things to read in our newsletter.
We combine our expertise with a fine knowledge of the industry to deliver high-value project management services.
MIGSO-PCUBED is part of the ALTEN group.
Find us around the world
Australia – Canada – France – Germany – Italy – Mexico – Portugal – Romania – South East Asia – Spain – Switzerland – United Kingdom – United States
© 2024 MIGSO-PCUBED. All rights reserved | Legal information | Privacy Policy | Cookie Settings | Intranet
Choose your language
Our website is not supported on this browser
The browser you are using (Internet Explorer) cannot display our content.
Please come back on a more recent browser to have the best experience possible
