Our website is not supported on this browser
The browser you are using (Internet Explorer) cannot display our content.
Please come back on a more recent browser to have the best experience possible

Information security is crucial for any organization, and as a company grows, so do its vulnerabilities towards security incidents. That was the case for our client, a world leader in pharmaceuticals, whose risk of a cybersecurity breach could harm both the organization and its patients.
Their role is to develop and commercialize new treatments for thousands of patients worldwide. Therefore, their patient and treatment data is sensitive and requires robust information security.
MIGSO-PCUBED was brought on board to improve the client’s cybersecurity measures quickly and to avoid a data breach. MP’s expertise in project and schedule management consulting was needed to build, manage, and execute the client’s Cybersecurity Transformation Program.
Read Also: Life Sciences Project Management
The pharmaceutical industry is entrusted with critically sensitive and valuable data about patients, research, patented drugs, clinical trials, and biomedical technology. This makes the pharmaceutical industry highly susceptible to cyber-attacks. Data breaches and ransomware alone costs the healthcare industry an estimated $4 billion in 2020.
With the number of cyber-attacks increasing globally, our pharmaceutical client sought to implement a robust cybersecurity program to safeguard their digital assets. The program’s goals also include improved security protocols, avoiding catastrophic loss of data, reduced downtime, and maintaining a safe and trusted environment.
The client had an existing Information Management PMO, which took ownership of the project. They worked with the information security team to create a roadmap for securing their digital environment. The MP team was then engaged to manage the entire stream of cybersecurity initiatives that this program relied on. We focused heavily on the schedule management component to deliver the program’s objectives as quickly as possible.
Our consultants began by working with IT System Owners to ensure the project’s scope and objectives were clearly defined and that the support team was well-established. Then the team worked through four phases to execute the project: Initiation, Analysis, Deployment, and Closure.
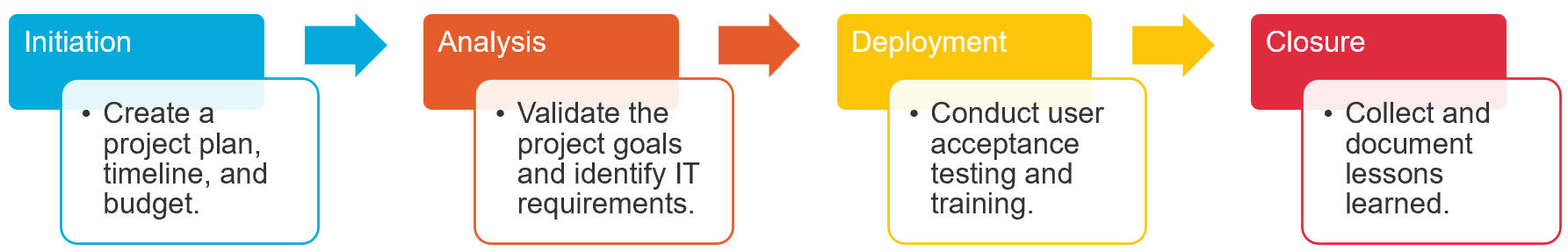
Our consultants held a scheduling kick-off meeting, which allowed them to create the project plan, set up the timeline in MS Project, and draft the project budget baseline. Then, the team constructed a project charter according to the client’s standard processes. They also worked with the legal team to begin the vendor procurement process. Finally, they developed a communication and risk management plan to share with the project team.
The consultants are responsible for working with the computer systems validation team. This team analyzes the goals of the project to understand whether the project needs to be a validated project or not. A validated project has a much more stringent process of documentation and verification to follow GxP and GDPR guidelines.
This steers the direction and timeline of every project. In response, the consultants needed to update their project plan to include tasks and deliverables for these activities. This phase also identifies the project IT requirements and system specifications. Therefore, it must be led by consultants with the technical knowledge needed to facilitate it.
Our consultants brought their expertise to conducting user acceptance testing for the new cybersecurity deliverables. Testing phases are often conducted in an agile fashion to ensure rapid testing and updates to the solution and deliverable(s). This was done smoothly by our consultants as they are well-trained in utilizing both Agile and waterfall principles. Once the consultants ensured approval from the system owner and responsible parties, the project was ready for deployment.
A consultant’s role was very crucial in this phase to keep the project deployment on track; deployment dates often depend on planned downtime of other systems.

During the Closure phase, our team held a retrospective session to collect and document lessons learned. All the financials were closed in the PPM tool and a final release memorandum was sent to the entire PMO team to finalize a successful project closure.
With our project management services, the client organization implemented a layered security strategy that includes basic protection policies, frameworks, and pioneering tools. This ultimately helped create a security culture with mindful employees.
After this project, MP’s actions allowed the client to back up, secure, and segment 8,317 systems. Moving forward, these systems are all outlined in a digital dashboard to track their current performance. Over 800 laboratory workstations were backed up, and the recovery time of a single workstation was reduced to under two hours.
And, in the case of catastrophic failure, full laboratory recovery became limited only by staff’s physical interactions with individual workstations. Now, a full restoration was reduced from approximately five months to one month. These improvements were found to benefit over 3,000 employees worldwide, along with every individual that the client supports.

Our client reduced downtime of systems and ensured every employee does their part to mitigate risks and avoid security concerns. This accomplishment was made possible with MP’s help to establish, manage, and control all projects within the cybersecurity program. Business continuity is now ensured for a company that manufactures lifesaving drugs and fortifies the company’s security.
For our client, this was an important transformation program worth more than 10 million dollars in total. Close to 30 projects were managed for the client by MIGSO-PCUBED over two years to successfully implement the cybersecurity transformation program.
The feedback from the management team following the transformation further showed their satisfaction with the project.
"Thanks to your effort and hard work on this initiative, [our] laboratory environment is now more robust and resilient to disasters."
Director of Scientific Platforms
“We have accomplished a major milestone to ensure system recoverability in the event of a catastrophic failure,” said the client’s Director of Scientific Platforms. “This project goes a long way to standardizing our approach to backups in our labs. This was a well-run and well-executed project. Thanks to your effort and hard work on this initiative, [our] laboratory environment is now more robust and resilient to disasters.”
Our client created a multiyear program to fortify themselves with effective security management capabilities, practices, and controls. Having a strong security program helped them to ensure confidentiality, integrity, and availability of all the data.
This article was written by Sirisha Pudipeddi and Lenard Norris
Loved what you just read?
Let's stay in touch.
No spam, only great things to read in our newsletter.
We combine our expertise with a fine knowledge of the industry to deliver high-value project management services.
MIGSO-PCUBED is part of the ALTEN group.
Find us around the world
Australia – Canada – France – Germany – Italy – Mexico – Portugal – Romania – South East Asia – Spain – Switzerland – United Kingdom – United States
© 2024 MIGSO-PCUBED. All rights reserved | Legal information | Privacy Policy | Cookie Settings | Intranet
Perfect jobs also result from great environments : the team, its culture and energy.
So tell us more about you : who you are, your project, your ambitions,
and let’s find your next step together.
Dear candidates, please note that you will only be contacted via email from the following domain: migso-pcubed.com. Please remain vigilant and ensure that you interact exclusively with our official websites. The MIGSO-PCUBED Team
Choose your language
Our website is not supported on this browser
The browser you are using (Internet Explorer) cannot display our content.
Please come back on a more recent browser to have the best experience possible
